At any given moment on any given day, are you able to confidently answer the question, “Are we protected?”
If you’re testing your security controls any less often than every single day, the answer to that question is a hard – and stressful – “no”. In the history of human technology, we’ve never had access to so much information, and the information we have has never spread so quickly from one endpoint to another. Your security environment is a dynamic, sometimes unpredictable place.
Maybe a decade or so ago, it was enough to conduct quarterly or even annual tests of your controls – but that’s not the case today. In an age where attackers are craftier, faster, and more equipped than ever before, how can defenders maintain a clear perspective on where their coverage stands – continuously?
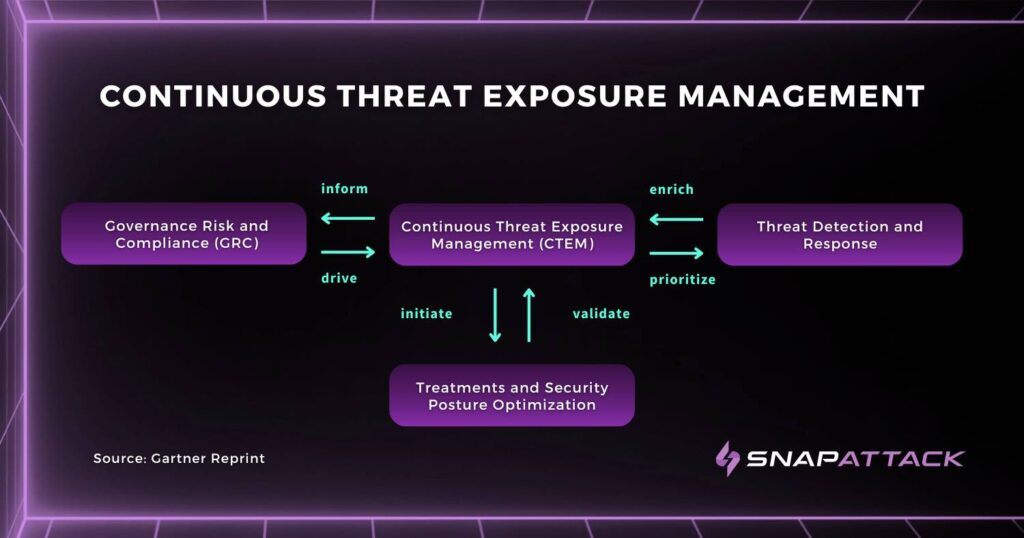
Continuous Threat Exposure Management: What Is it and Why Does It Matter?
Gartner® recently addressed this industry-wide challenge by introducing a framework called Continuous Threat Exposure Management (CTEM). CTEM is an approach that helps defenders self-assess their system’s vulnerabilities via attack simulations, red teaming, and other threat management methods.
CTEM empowers businesses to continuously evaluate their security posture and spot weaknesses before bad actors can exploit them. That means that security teams can avoid the costs, chaos, and complete upheaval of their operations they would suffer from a breach altogether.
With an endlessly growing attack surface, CTEM provides a methodical approach that enables organizations to properly prioritize possible threats and related remediation operations in a continuous manner. And the cybersecurity community has taken notice – Gartner has named CTEM as one of its top Cybersecurity Trends for 2023.
The CTEM Cycle Explained
1. Scoping
To get started, teams must see themselves from a threat actor’s perspective. CTEM begins with establishing a thorough, contextual understanding of the risks businesses face in their security environment and which ones pose the greatest threat. From there, they can determine where their efforts will be best spent in lowering or managing risk scores, broken down by organizational segment.
2. Discovery
Most security teams already receive data from threat detection and monitoring tools like SIEM, XDR, or EDR. By analyzing that data, security teams can evaluate their attack surfaces, high risk assets, attack vectors, vulnerabilities, and business impact of both on-premises and cloud environments. However, the average SOC is drowning in false alerts and takes in an endless volume of data every day – they need to know where their efforts are best spent.
3. Prioritization
This is where scoping and discovery converge. After they’ve aggregated data from the sources listed above, defenders prioritize their vulnerabilities according to the gaps they identified in their environment. Teams can use frameworks like the MITRE ATT&CK® coverage matrix to determine where they need to focus their defensive strategy.
By prioritizing early on, security teams can sift through the barrage of alerts they see every day and focus on the threats that matter most to their specific environment.
4. Validation
Once exposures have been identified, it’s time to test controls against them and make sure defenses are prepared before a threat actor strikes. Through methods like attack simulation or emulation, pen testing, and purple teaming, security teams can answer the question, “Are we protected?” in a risk-free environment.
5. Mobilization
With a thorough understanding on where their coverage truly stands, teams can improve and bolster their security defenses, strategy, and processes as necessary. Remember, CTEM is a continuous framework, which means the work is never really done – monitor performance relative to baselines, benchmarks, and risk profiles to ensure you stay protected over time.
Whether they are a part of an ongoing vulnerability management program or another proactive security posture initiative, most enterprises are already fulfilling some of these steps in some way.
But to enable and empower security teams to make better decisions for their unique environment, it is crucial to think of this endeavor as a combination of people, procedures, and technology continuously working together. It must be bought into at the organizational level, not seen as a collection of technical fixes deployed to address a singular, isolated problem.
Empower your security teams through continuous, centralized workflows – check out out recent eBook:
Streamlining the Threat Detection Development Lifecycle.
How SnapAttack Enables CTEM
Continuous models like CTEM require technology that integrates and communicates with the rest of the company’s tech stack. Unfortunately, that’s just not how most of the tools on the market are designed. But SnapAttack is different.
SnapAttack helps teams continuously assess their detection estate as it evolves alongside today’s threat landscape. SnapAttack’s dynamic approach to threat management empowers teams to follow the CTEM framework and maintain constant visibility into their most pertinent threats.
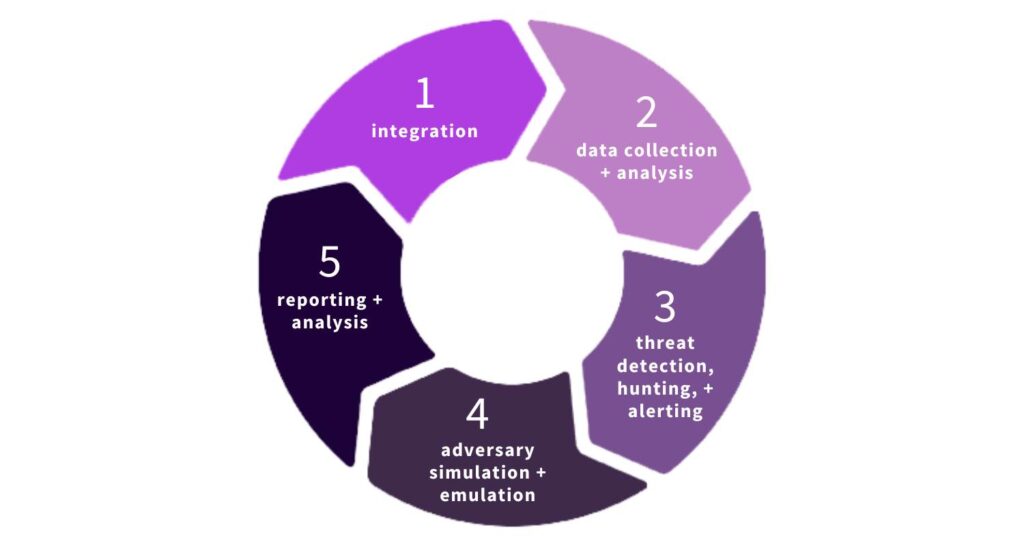
Here’s how we’ve adapted Gartner’s CTEM framework in our platform:
- Integration (Scoping)
- Data Collection and Analysis (Discovery)
- Threat Detection, Hunting, and Alerting (Prioritization)
- Adversary Simulation and Emulation (Validation)
- Reporting and Analysis (Mobilization)
1. Integration (Scoping)
SnapAttack’s integration into users’ existing security infrastructure and monitoring systems makes CTEM intuitive and actionable. Users have the ability to integrate with existing security information and event management (SIEM), XDR, and EDR systems (or other included toolsets) or establish communication channels for threat intelligence sharing directly through the SnapAttack app.
2. Data Collection and Analysis (Discovery)
SnapAttack users can continuously monitor and collect data from the various sources in their network, such as network traffic, system logs, threat intelligence sources, and endpoint activities. They’re able to leverage the platform to analyze this data for threat hunting or detection engineering, using techniques like behavioral analysis, anomaly detection, or signature-based identification with our no-code detection building abilities.
3. Threat Detection, Hunting, and Alerting (Prioritization)
Our users can address potential threats by analyzing tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) based on their collected data. Using those indicators, they can determine which threats are most prevalent and severe in relation to their systems, and easily validate their coverage with our library of pre-built detections.
Also, analysts using detection engineering methods can define rules, patterns, or algorithms that trigger alerts or notifications in enterprise tools when suspicious activities or anomalies are detected. This enables security teams to take timely action based on detections or hunt activities – BEFORE the damage is done. Teams can accurately and consistently measure their coverage and adjust their approach by mapping their environment to the MITRE ATT&CK® matrix – directly from the app.
4. Adversary Simulation and Emulation (Validation)
Security teams spend significant funds on automation and tooling in this area, whether it’s for red/purple teaming, attack route analysis, or breach attack simulation (BAS). The idea is to behave and think like a bad actor to evaluate how well their current security controls are working. In our platform, this can be achieved by integrating SnapAttack within the broader incident management lifecycle.
When threat detections are created, teams need to prove they work. This is a critical step that helps the organization truly understand their preparedness for any given threat. It can be challenging to do without the right automation linking the offensive testing to the broader security ecosystem – teams that operate security tools like SIEMs, EDRs, and incident management platforms (and teams) often struggle to get the most value out of adversary simulation without such integration. SnapAttack equips users to validate their coverage right in the app using our adversary emulation, simulation, and streamlined validation script builder – risk-free and faster than ever.
5. Reporting and Analysis (Mobilization)
Users can leverage SnapAttack’s reporting and analytics capabilities to generate insights on threat trends, incident patterns, and system vulnerabilities. They can then action their findings to fine-tune their CTEM program, improve their overall security posture, and implement proactive defenses for threat prevention.
Conclusion: Achieve Proactive Threat Management with CTEM
Continuous Threat Exposure Management is a new framework taking security by storm, backed by Gartner and other leaders in our industry. It addresses some of our community’s greatest challenges to proactive defense through visibility, contextual awareness, and preventative coverage. It’s more comprehensive than traditional approaches like attack surface management and breach attack simulation, without distracting from the overall security posture of the organization.
In reality, CTEM is more than a framework. It’s a mindset that guides security teams away from retroactive solutions and towards a more comprehensive, proactive threat management program – a mindset that all security teams strive for, but few actually maintain.
Is CTEM just the latest buzzword that’s captured the cybersecurity community? Or is it a sign that real change is underway – LASTING change that will benefit defenders everywhere? We lean towards the latter – because this is the kind of change SnapAttack was designed to inspire in our users.
Our platform makes CTEM and other security frameworks, like threat hunting, detection engineering, and purple teaming, easier and more intuitive than it’s ever been. You can get a preview of how we do that in the Community Edition of our platform – completely and forever free of charge.




