threat intelligence
Not your father's threat intelligence.
Prioritization, specificity, and actionability are common challenges with threat intelligence. With SnapAttack, they aren’t – no matter your team’s skillset.

Quickly understand which threats matter to you.
Progress past the IOC and easily action TTPs.
Make it easy for detection engineers and key stakeholders to take their next steps.
Threat intelligence BEFORE and AFTER SnapAttack:
BEFORE
- You’re approaching threat intelligence like a box you have to tick.
- You struggle to determine which intelligence is relevant and important.
- You're limited to hunting IOCs like IP addresses, hashes and domain names.
- You're paying for multiple threat intelligence services, but they're really just IOC feeds - and you’re still missing actual incidents.
- Your hand-off from intelligence to detection engineering is cumbersome, limited, and lacking the detail needed for real action.
AFTER
- Behavioral threat intelligence is a key piece of your detection strategy.
- Your priority threats are known and documented, and you know exactly how you'd stand up against them.
- You can quickly hunt for TTPs (and IOCs) directly in your detection tools, without deep technical expertise.
- You can report upon and drive improvement of coverage against the threats that matter to your strategic stakeholders.
- Threat intelligence hand-offs to detection engineering are seamless, efficient, and quick to action, creating a united front against the threats that matter.
the threats that matter
Stop wasting your time playing whack-a-mole with IOC feeds that are outdated the minute they're published.
Start applying priority threat intelligence that's tailored to your organization.
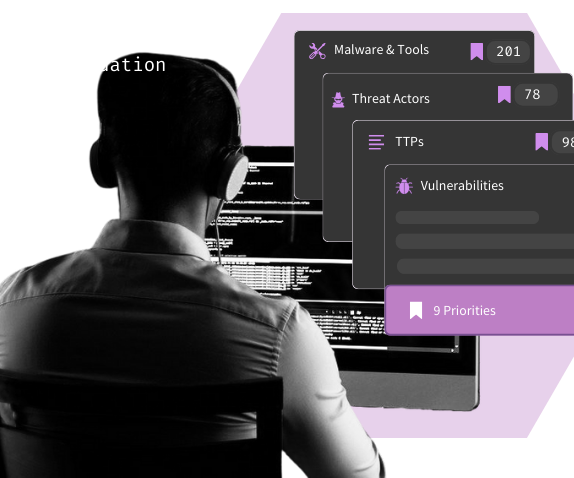
Identify detection blindspots with your Threat Profile
You tell us key information about your organization and tech stack, and SnapAttack tells you the threats you need to care about (and how to shut them down with ease).
Speed up threat research with centralized Threat Dossiers
Learn everything you need to know about a threat actor, vulnerability, attack tool or technique with Threat Dossiers, driven by machine learning (ML) and Mandiant Threat Intelligence.
Have your security teams work smarter, not harder.
Case Study:
Empowering In-House Cybersecurity Excellence at a Fortune 500 Bank
quickly and easily
Stop wondering what your next steps are with outdated, stagnant threat intelligence.
Start progressing past IOCs and actioning TTPs immediately (without a cyber ninja skill set).
Map your threat priorities to the MITRE ATT&CK Matrix
Understand where you need to investigate further with the MITRE ATT&CK matrix, mapped to your environment and your priorities - even as your coverage evolves.
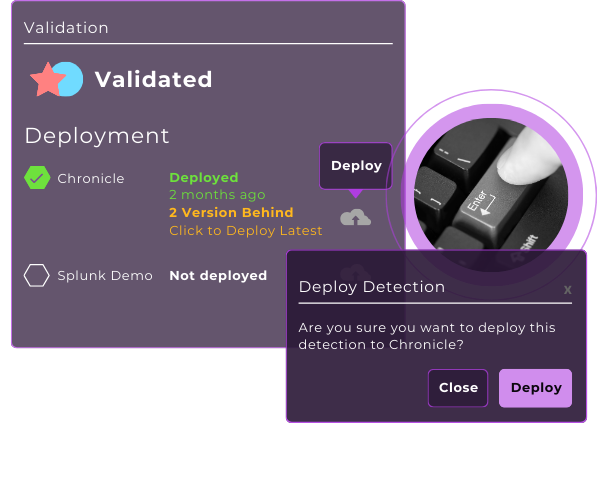
Action TTPs and IOCs across your detection stack
Hunt, alert, and validate TTPs (and IOCs) in just one click to instantly and easily identify advanced threat actors.
your threat intelligence program
Stop investing in threat intelligence that fails to drive action on the ground.
Start addressing your high-priority coverage gaps with threat intelligence driven by your security needs.
Accelerate your next steps
It’s simple to hand behavioral threat intelligence off to detection engineers, threat hunters, and the SOC so they can take it and run wherever they need to - without requiring decades of technical expertise.
Easily report to internal stakeholders
Give your strategic intelligence stakeholders everything they need to make informed decisions about the threats that are impacting your industry before they impact you.

Which threats are most relevant to your industry?
Free Industry-Specific Threat Report

VP of Threat Management at a major financial institution
why snapattack?
Threat intelligence should drive your entire threat management strategy, not just sit on the shelf.
IOCs alone aren’t going to cut it against today’s sophisticated threat actors. Here’s how we promise to level up your team:

Fast time to value.
Get more from your teams and more from your tools with built-in training and 30+ direct integrations.
Try before you buy.
We want to make sure we’re a good fit. That’s why you get a POV that reflects your unique environment before you sign off on ANYTHING with us.
Easy to use, easy to scale.
Cybersecurity is for everyone - that’s why SnapAttack is easy for even junior analysts to navigate with built-in training to keep up with your team’s skillset as you grow.
Expert support at your fingertips.
Our customer success and product teams are available via Slack and regular check-ins to make sure you’re getting everything you need out of our platform.
services
Find out where you stand and how to modernize your SOC so you can take action against against the threats that matter most, faster.
Threat Intelligence Maturity Assessment
Many organizations lack the time and maturity to move from stagnant, reactive intelligence to actionable, TTP-based detections.
Allow our team of experts to uncover opportunities in your processes, technology, and threat inputs to optimize your SIEM for TTP-based detection.
Threat Hunting Maturity Assessment
Make the most of your threat hunting time and budget, and measurably improve your maturity.
Find out where your threat hunting program stands, where your critical gaps lie, and how you can detect more relevant, sophisticated threats faster.
MITRE ATT&CKTM Assessment
Few companies know where their MITRE ATT&CK technique coverage stands…and without it, they can’t tackle their urgent security gaps.
Identify your blindspots and the actions you need to take in order to get them covered, with expert guidance and dynamic measurement.
resources
Modernize your threat intelligence with our popular resources:
And see how it’s done in our Threat SnapShots:
explore our other use cases
threat hunting
Proactively reduce risk across your attack surface – even within large, decentralized environments.
detection engineering
Deploy rapid detection coverage for the threats that matter most.
siem migration






