platform
Answer your most pressing threat questions with one unified platform.
Paint a complete picture of your threat priorities.
A central hub that unsilos your teams and tools, powered by a horizontal workflow that just makes sense. SnapAttack gives your intelligence, detection engineering, and hunt teams more of their most precious resource – time.
Unlock your defenders’ full potential by removing barriers, filtering out the noise, and prioritizing the work that matters.
your current coverage
Answer the question: “Where are my detection gaps?”
The Problem: Disparate point solutions make it hard for companies to know which threats they can see and which they’re likely to miss – and without knowing where you’re at, it’s impossible to know how to improve.
SnapAttack’s Solution: By mapping your coverage against MITRE ATT&CKTM , your SnapScore shows you where you stand and where you have gaps, bringing every blindspot to light.


Assess your coverage and reduce attack surface exposure by up to 91%. Here's how:
Determine the threats that matter with your Threat Profile.
Understand your current protection against them with SnapScore.
Map your detection gaps to MITRE ATT&CK.
the threats that matter
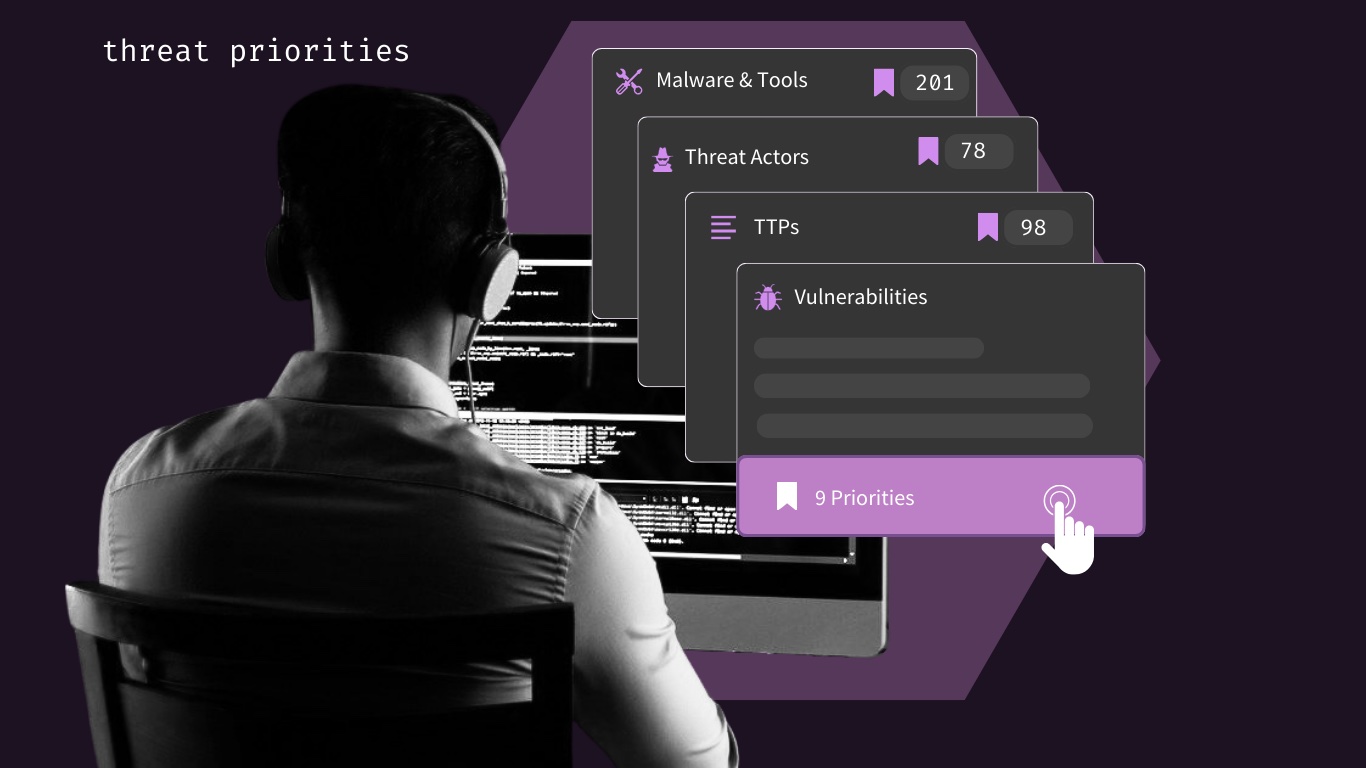
Answer the question: “Which gaps matter to us most?”
The Problem: There’s never a shortage of to-dos within a SOC… but knowing where to start can be tricky.
SnapAttack’s Solution: By pairing next-gen threat intelligence with your organizational context and tooling, SnapAttack’s AI and ML-powered algorithms tell you what matters, where to start, and what’s next.

Prioritize what matters most and reduce mean-time-to-detect by 93%. Here’s how:
Find out everything you need to know in our Threat Library.
Get a starting point with Threat Priorities.
Pivot from understanding to action with the Action Recommendation Engine.
the right defenses
Answer the question: “How do we fill those gaps?”
The Problem: You’re wasting too much time in the weeds of research or pivoting between tools.
SnapAttack’s Solution: Whether you need to hunt an actor shown in your threat profile, deploy an alerting rule to your SIEM or EDR, or validate that your SOC is going to alert on malicious activity, SnapAttack’s workflow, automation, and integration make it easy to streamline research and take action faster and more easily.
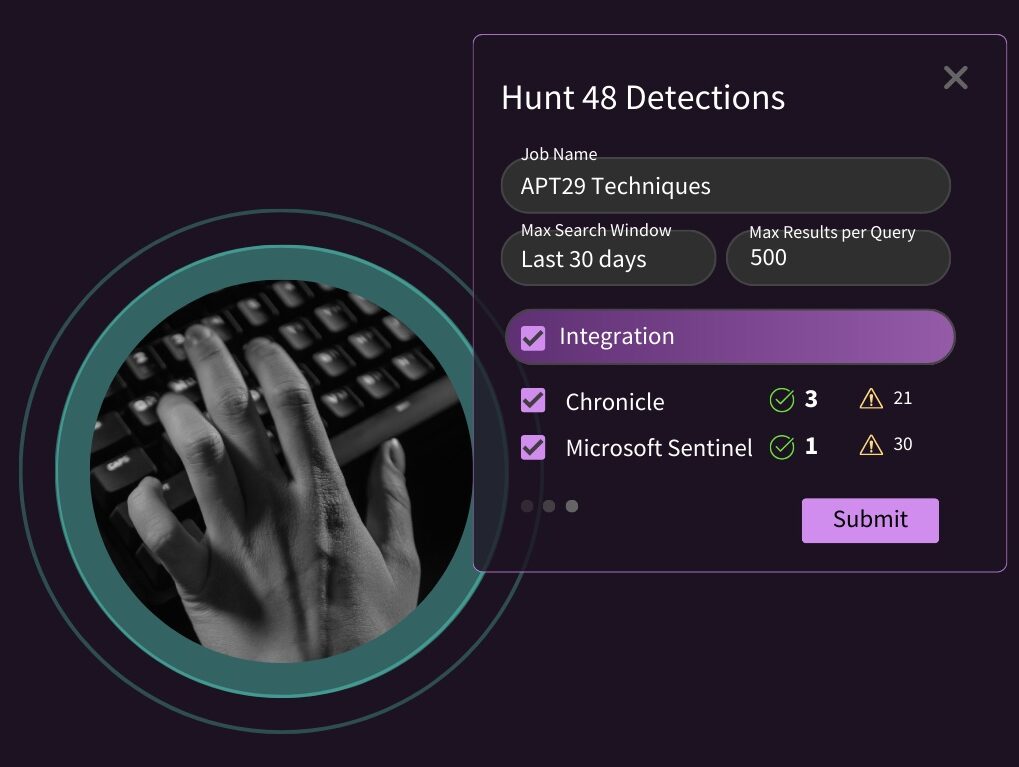

Move from intelligence to action 98% faster. Here’s how:
Accelerate defense mobilization with Recommended Detections (or build your own).
Deploy alerting rules in just one click with API Integrations.
Remove the friction from threat hunts with the Hunter’s Workbench.
that you’re protected
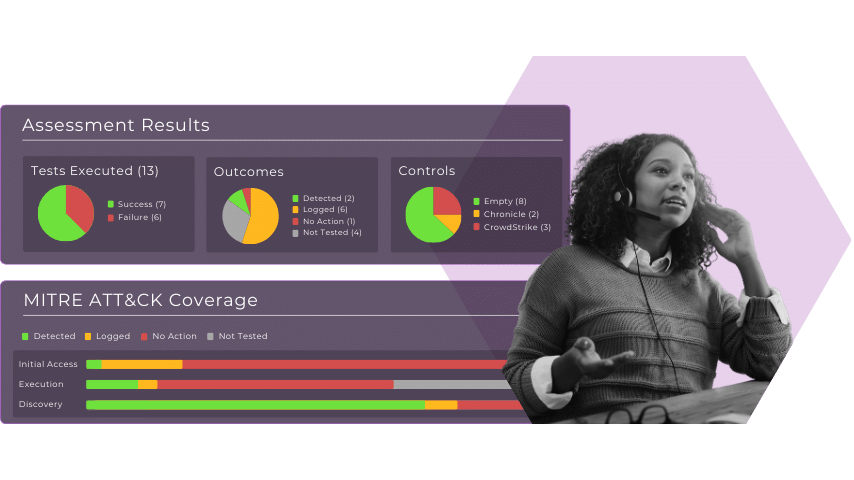
Answer the question: “Are we protected?”
The Problem: When it comes to answering this question, hope is not a strategy. There’s a lot riding on your ability to detect malicious activity – you need to prove it works.
SnapAttack’s Solution: With SnapAttack, you don’t need an army of red teamers or a complicated tool that tests every possible attack path. We make it simple to bake validation into your detection life cycle with attack scripts informed by threat intelligence, accelerated by automation, and organized by the things you care about.

Get 65% more TTP coverage than out of the box SIEMs. Here’s how:
Eliminate the red team blue team divide with the Attack + Detection Library
Get an extra layer of reassurance with the Validation Engine
dynamic, continuous defense
Answer the question: “How do we STAY protected?”
The Problem: As the threat landscape evolves alongside your attack surface, you need the visibility to see ineffective or obsolete detection rules… and the structured workflow to maintain them amidst environmental drift.
SnapAttack’s Solution: Get the centralized visibility and timely intelligence you need to continuously validate, maintain, and expand your coverage over time, yielding the resilience your threat detection program needs.
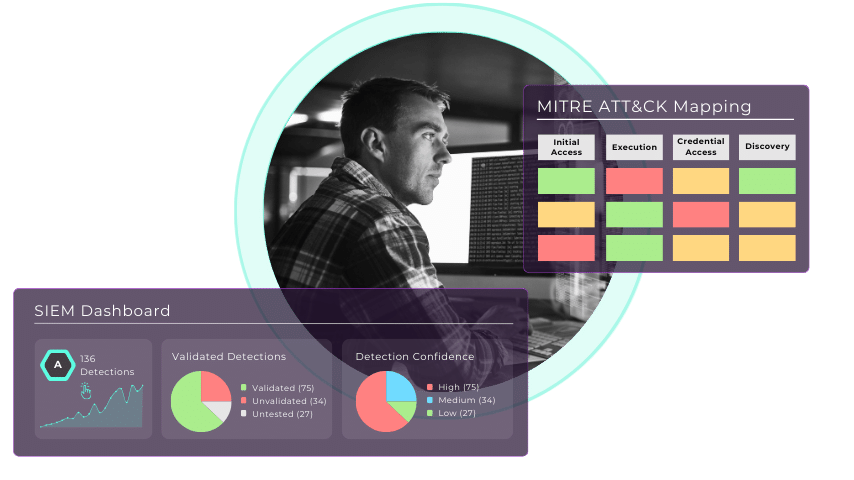

69 zero-days disclosed so far this year (and counting). Are you keeping up?
Stay up-to-date with industry-leading threat intelligence.
Stay on top of your coverage with real-time dashboards for every role.
use cases
threat
hunting
Proactively reduce risk across your attack surface – even within large, decentralized environments.
detection engineering
Deploy rapid detection coverage for the threats that matter most.
threat intelligence
Operationalize expert threat research that’s actually relevant to your organization.
siem migration and optimization
Prioritize, expand, continuously validate, and report on MITRE ATT&CK coverage, without the alert fatigue.
use cases
threat hunting
Proactively reduce risk across your attack surface – even within large, decentralized environments.
detection engineering
Deploy rapid detection coverage for the threats that matter most.
threat intelligence
Operationalize expert threat research that’s actually relevant to your organization.
siem migration
Prioritize, expand, continuously validate, and report on MITRE ATT&CK coverage, without the alert fatigue.
Get everyone on your team to the next level (yes, everyone).
for security leaders
Measure and optimize your tools, teams, and defenses in one continuous workflow that shows you where your blindspots are and how your team can mobilize to fill them, instantly and easily.
for security teams
Work smarter, not harder with actionable threat intelligence designed for threat hunters and detection engineers that helps them hunt, detect, respond, and validate with the speed and precision of cyber ninjas.
why snapattack?
There are enough barriers to threat-informed defense. We’re here to help you tear them down.
Point solutions kill your ROI, team morale and productivity, and worst of all, your visibility and protection. SnapAttack was built to bridge together your point solutions, level-up your teams, and unify your security operations so that you can stay ahead of the threats facing you.


Fast time to value.
Get more from your teams and more from your tools with built-in training and 30+ direct integrations.
Try before you buy.
We want to make sure we’re a good fit. That’s why you get a POV that reflects your unique environment before you sign off on ANYTHING with us.
Easy to use, easy to scale.
Cybersecurity is for everyone - that’s why SnapAttack is easy for even junior analysts to navigate with built-in training to keep up with your team’s skillset as you grow.
Expert support at your fingertips.
Our customer success and product teams are available via Slack and regular check-ins to make sure you’re getting everything you need out of our platform.
Have your security teams work smarter, not harder.
Case Study:
Empowering In-House Cybersecurity Excellence at a Fortune 500 Bank
platform plans
PRO
Enhance threat detection with curated content developed by experts.
Premium validated, behavioral threat detection content
Thousands of real-time attack sessions
Custom dashboards
Up to 2 SIEM + EDR integrations
Next-gen threat intelligence
PLUS
Accelerate your ability to develop detection content with expert and open-source threat research.
All the benefits of our Pro tier plus:
Accelerate custom content development and build detections-as-code
Emulate attacks in-app or in your environment
Equip your existing security validation platform
COMPLETE
For large organizations in either the public sector or private sector who want access to all of SnapAttack’s platform capabilities.
All the benefits of our Plus tier plus:
Build and launch control validation scripts
learn more
Frequently Asked Questions (FAQs)
While individuals such as detection engineers, threat hunters, threat researchers, students, and others do find value in our platform – the most efficiency gains and highest return on investment are felt by InfoSec teams that adopt our full suite of capabilities as a team (from CISOs & SOC Managers to Red & Blue teams).
Absolutely! Our Community Version is a great place to start. Click HERE to gain free access.
We integrate with over 35 of the leading SIEM & EDR/XDR platforms. Most of the industry’s favorites are already supported. You can see the full list here.
Some of our deepest integrations include Splunk, Azure Sentinel, Crowdstrike, SentinelOne, Chronicle, MDE and Elastic.
For unsupported integrations – we are always happy to consider expanding the integrations set based on customer request. When feasible, we can usually add integrations in 4-6 weeks.
There is some level of SOC maturity that we recommend in order to realize the most value out of our platform. That said, we’ve found that customers leverage the platform in different ways depending on where they stand in their journey through security operations maturity.
For those early in the journey, we enable junior analysts to advance their skillsets quickly, augment many of the red & blue team functions, and serve as a powerful content management feed for detection analytics, hunt queries, and threat emulations.
The more mature customer can leverage much more of our advanced toolset – red teamers lean on our Attack Capture Lab for attack emulation, detection engineers build and deploy analytics in our no-code detection builder, and purple teamers automate and collaborate with our Attack Plans.
Absolutely – our mission is to ensure you can get more value out of the teams and tools you already have. Tools like EDR, XDR & SIEM are supercharged and validated by SnapAttack’s platform.
Absolutely, and many do. While SnapAttack does offer advanced security validation capabilities, we lean heavily on this functionality to allow our customers to verify that their detection pipeline in the platform is validated and working as it should.
With this in mind, we have plenty of customers who leverage validation scripts from their existing BAS tool in the SnapAttack platform, and benefit greatly from our detection content and hunt queries in parallel.
We cover multiple use cases across the cybersecurity spectrum for anyone requiring a Proactive Threat Management Platform.
Enterprise & Public Sector CISOs, SOC Managers, Red & Blue Teams, Detection Engineers, Threat Hunters & Purple Teams find the most value from the SnapAttack platform.
MSSPs, Consultants & IR Firms also find tremendous value in delivering their services at scale, effectively and consistently across disparate tooling.
Absolutely! Once you’re in the app, you can create intelligence products by uploading a resource (PDF or link) to prepopulate your form or manually entering it in.
SnapAttack has log sources originating from Windows and Linux hosts.
Absolutely! When you input your native detections, your organization will even be credited for your threat hunting efforts (which affects your overall health score on the Detections Dashboard!).
SIGMA rules are synced with SnapAttack every six hours.
The SnapAttack platform supports “bulk ranking” which provides customized rankings based on your existing environment.


