threat hunting
Hunt your blindspots (without the guesswork).
Accelerate threat hunting with the intelligence, the tools, and the workflow to determine which threats matter and how to track them down faster.
Identify threats and prioritize hunts with precision.
Simplify the process from understanding a threat to protecting against it.
Accelerate time to triage with centralized hunt results.
Threat hunting BEFORE and AFTER SnapAttack:
BEFORE
- You need an advanced skillset and years of experience to hunt.
- Your only guideposts are the ever-changing headlines.
- You spend days researching threat intelligence across several sources.
- You’re copying and pasting IOCs.
- You’re chasing false alerts your EDR isn’t designed to catch.
- You’re pivoting between spreadsheets to triage data.
You’re stuck with reactive, aimless threat hunting and decentralized results that are hard to communicate across the SOC.
AFTER
- Your whole team has a cyber ninja skillset.
- You can visualize urgent coverage gaps and prioritize hunts.
- You can quickly operationalize frontline threat intelligence.
- You can instantly draw out relevant TTPs and IOCs.
- You can threat hunt across your disconnected tools in one click.
- Your hunt program is centralized and you can articulate results across the organization.
You’re proactively hunting your highest priority threats with a process that’s fast, easy, and actionable for every role on the team.
your most pressing threats
Stop playing catch-up with the latest threat of the week.
Start focusing on the threats that matter most with speed and precision, whether they’re emergent or evergreen.
Determine the threats that matter with Threat Profiles
Discover where you have detection gaps based on factors like your industry, tech stack, region, risk threshold, and more.
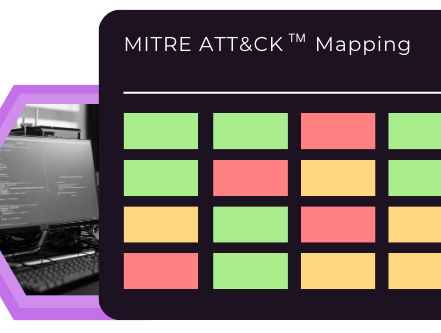
Identify blindspots with the MITRE ATT&CKTM Matrix
See where you stand against advanced threat actors with a real-time view of your coverage mapped to the TTPs the adversary is known to use.
with proven detection content
Stop wasting time on exhaustive threat research, hunt hypotheses, and queries.
Start hunting immediately with detection content that's proven to work for you.
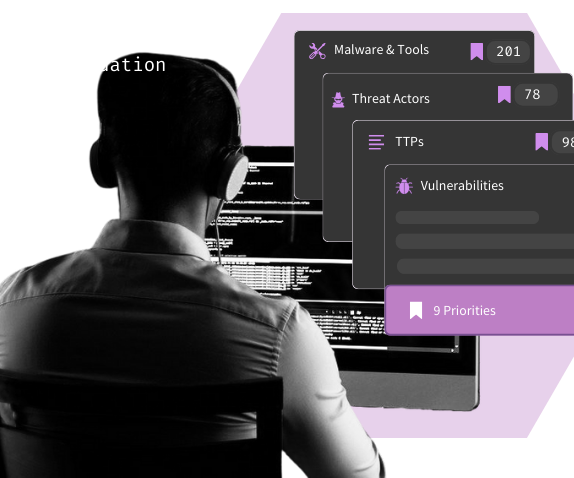
Learn everything you need to know about any given threat with Threat Dossiers
No matter what you’re hunting, we put adversary techniques on blast so you can burn them with ease - across all your tools, in one click.
Mobilize quickly with the Action Recommendation Engine
Machine learning (ML) filters our 10k+ detections down to serve you up the best detection strategies for the threats you care about in the environments you're hunting in.
your hunt program
Stop pivoting between spreadsheets and browser tabs to view hunt results.
Start centralizing hunts so you can easily triage and identify next steps.
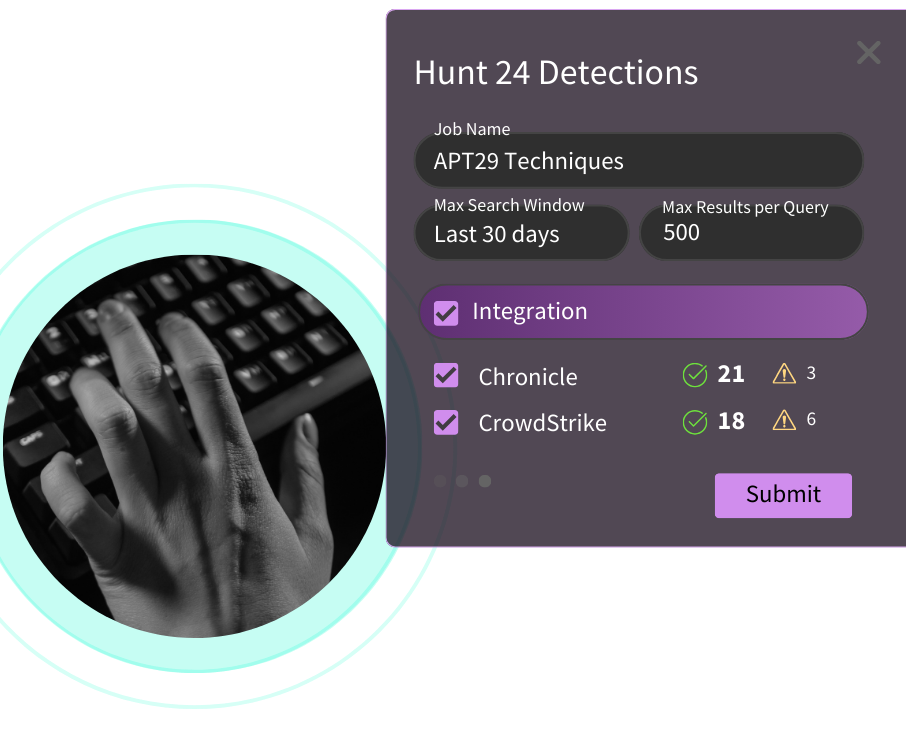
Hunt any given threat across all of your tools with ease in the Hunter's Workbench
Centralize your hunt process across your disconnected SIEMs, EDRs, and datalakes to get to the finish line faster.
Accelerate your next steps
Whether your next step is containment and eradication, or reporting results to leadership, we'll make it easy.

Andrew Danis
Deputy Federal Lead, Cyber Security Operations & Threat Mitigation & Incident Response (TMIR)
National Institutes of Health
why snapattack?
SnapAttack was built by threat hunters FOR threat hunters.
That means we know where your previous threat hunting tools have fallen short. Here’s what we can promise you with SnapAttack:

Fast time to value.
Get more from your teams and more from your tools with built-in training and 30+ direct integrations.
Try before you buy.
We want to make sure we’re a good fit. That’s why you get a POV that reflects your unique environment before you sign off on ANYTHING with us.
Easy to use, easy to scale.
Cybersecurity is for everyone - that’s why SnapAttack is easy for even junior analysts to navigate with built-in training to keep up with your team’s skillset as you grow.
Expert support at your fingertips.
Our customer success and product teams are available via Slack and regular check-ins to make sure you’re getting everything you need out of our platform.
services
Whether your goal is to take your threat hunting program to the next level, or build a threat hunting program from the ground up, SnapAttack can help.
Threat Hunting Maturity Assessment
Make the most of your threat hunting time and budget, and measurably improve your maturity.
Find out where your threat hunting program stands, where your critical gaps lie, and how you can detect more relevant, sophisticated threats faster.
MITRE ATT&CKTM Assessment
Few companies know where their MITRE ATT&CKTM technique coverage stands…and without it, they can’t tackle their urgent security gaps.
Identify your blindspots and the actions you need to take in order to get them covered, with expert guidance and dynamic measurement.
Threat Hunting as-a-Service
Some organizations don’t have the bandwidth to threat hunt in-house, but that shouldn’t hold you back from proactive defense.
Let our experienced team of threat hunters detect and shut down your most critical threats, without any extra effort from you.
resources
Unlock a proactive threat hunting strategy with our popular resources:
And see how it’s done in our Threat SnapShots:
explore our other use cases
detection engineering
Deploy rapid detection coverage for the threats that matter most.
threat intelligence
Operationalize expert threat research that’s actually relevant to your organization.
siem migration




