SnapAttack’s Threat Hunter’s Workbench: Revolutionizing Cybersecurity with Advanced Threat Hunting and Detection

In today’s rapidly evolving digital landscape, the battle between cyber attackers and defenders has reached new heights. Cyber threats have become more sophisticated, targeting organizations of all sizes and industries. To stay ahead of these threats, organizations require innovative and powerful cybersecurity solutions that empower their security operations teams to proactively hunt down and detect […]
Continuous Threat Exposure Management (CTEM): A Proactive Cybersecurity Model
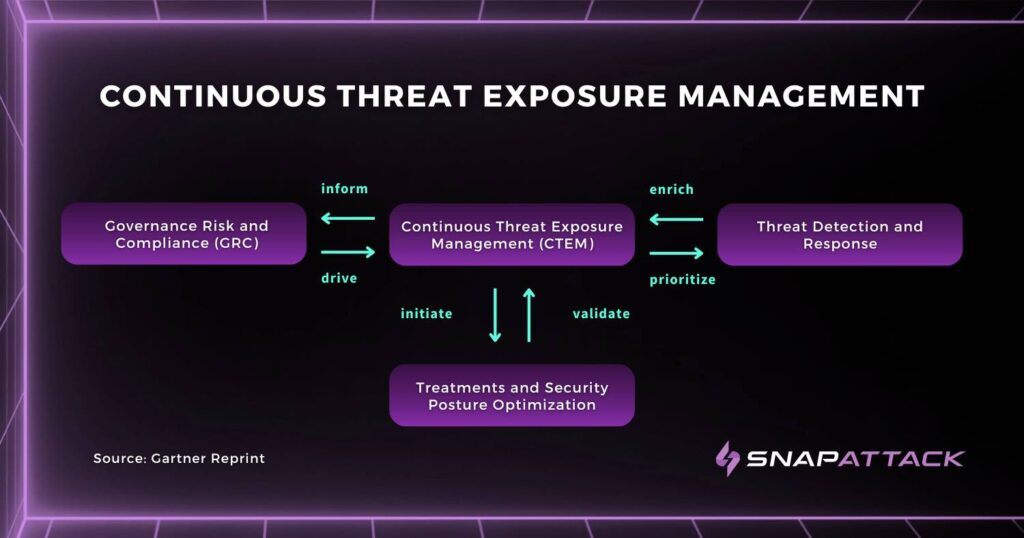
At any given moment on any given day, are you able to confidently answer the question, “Are we protected?” If you’re testing your security controls any less often than every single day, the answer to that question is a hard – and stressful – “no”. In the history of human technology, we’ve never had access […]
SnapAttack Platform Plans

DOWNLOAD NOW > What’s in this Datasheet? Operationalize threat detection today with any of our plans. All of our subscriptions can be tailored to your tech stack and security landscape to power up and streamline your threat detection. DOWNLOAD >
What is Purple Teaming?

Traditionally, red and blue teams work in silos, guided by competing goals. While the red team conducts offensive drills like pen tests and ethical hacking, the blue team strengthens defenses and responds to incidents. Because of this divide, red and blue teams have developed a naturally adversarial dynamic – but when the two work together, […]
How to Operationalize Cyber Threat Intelligence

The problem with threat intelligence isn’t that it’s hard to find.It’s not that there isn’t enough of it out there.And it’s certainly not that it doesn’t matter – at least 95% of CISOs agree that it’s a priority.In fact, the problems with threat intelligence are quite the opposite. Most of the time, there’s just too much […]
Better Together

Get your access to the webinar recording: Duration: 56 minutes | Partnering webinar with: Mandiant/Google, Stairwell, Nozomi Networks, SentinelOne, and Corelight About the Webinar Hackers have mastered the art of working together to become smarter, faster, and more efficient – without the red tape we have in our corporate infrastructure. So at RSAC 2023, […]
Strengthening Security through Collaboration: A Guide to Purple Teaming

What’s in this eBook? Red and blue teams tend to operate in a natural divide, keeping offensive and defensive measures in separate silos. But without clear visibility and communication, teams receive a disjointed view of their cybersecurity posture. Purple teaming bridges the gap between red and blue teams to result in a dynamic, comprehensive, and […]
How to Become a Cyber Threat Hunter: A Guide to Level Up Your Security Team

What is Threat Hunting? And Why Are Threat Hunters in Such High Demand? According to Splunk’s 2023 State of Security report, the median time from compromise to detection is nine weeks. Mandiant’s 2023 M-Trends report clocks median dwell time at 16 days. Either way, both numbers are FAR too high – and the damage a […]
Proactive Threat Hunting at Scale: Why It’s Important and How to Do It

Why Proactive Threat Hunting? When the average data breach costs organizations over $4 million, a proactive cybersecurity posture isn’t just nice to have – it’s essential. But traditional cybersecurity frameworks tend to be reactive in nature, remediating attacks that have already occurred rather than identifying potential risks that may impact the organization down the road. […]
Solutions for Purple Teams

Threat-informed defense. Powered by purple.
