Ask any security leader and they’ll tell you actionable threat intelligence is the cornerstone of a successful, threat-informed security operations center (SOC). However, to be of any real value to the team, threat intelligence needs to be relevant, timely, and supportive of next steps for the teams that utilize it. Due to the sheer volume of threat intelligence and the challenges teams face to try and sift through it all, teams can’t easily find and action the intelligence that really matters…leaving reports unhelpful and unused. In fact, a recent report found that 93% of CISOs are concerned about dark web threats, but almost ¼ of CISOs have no threat intelligence capability at all.
Because threat intelligence analysts are siloed from other core functions in the SOC, like threat hunting, detection engineering, and incident response, they frequently package up their findings in verbose reports and struggle to prepare threat intelligence reports in a manner that’s meaningful to those advanced team members. As a result, threat intelligence reports don’t always contain the actionability or clear next steps that teams need to mobilize. In the end, reports can eat up a significant proportion of the security budget and amount to nothing more than shelfware (expensive shelfware).
To reap the full value of threat intelligence and utilize it to mobilize against relevant threats, analysts and hunters need to be on the same page from the start. Actionable threat intelligence contains significant information on which threats may impact the organization and how they might manifest; by understanding the threat hunters’ needs, goals, and approach to the hunt, threat intelligence analysts can prepare reports that transform the SOC into an intelligence-led, threat-informed organization.
- Tactical threat intelligence involves the investigation and identification of IOCs to guide network level action to remediate threats. It enables analysts to look at threats on a more individual level.
- Strategic threat intelligence incorporates the broader threat trends in the context of the organization. This discipline helps teams calculate the risk and potential impact of threats as they relate to the strategic direction of the organization.
- Operational threat intelligence is intelligence for threat hunters. It’s the work they do to catalog adversary behavior and determine complete remediation of the threat at hand. It provides them with a roadmap to take action against the adversary.
The Disconnect Explained: Where Does Threat Intelligence Fall Short?
Threat intelligence analysts and threat hunters share the same overall goal: protect the organization. So while they’re aiming for the same target, where (and why) are they missing each other?
Threat Intelligence Disconnect #1: IOCs vs. TTPs
Additionally, the report will likely include a selection of IOCs that can be deployed as SecOps queries, but the questions remain: are they comprehensive? Have they been adequately enriched to determine maliciousness? As a reader, the hunter is left with more questions and work left to do rather than concrete answers and next steps.
Threat Intelligence Disconnect #2: Lack of Technical Alignment
Threat Intelligence Disconnect #3: Outdated Information
Threat Intelligence Disconnect #4: Strategic Misalignment
- Threat modeling
- Threat profiles
- MITRE ATT&CK mapping
How to Create Actionable Threat Intelligence for Threat Hunters
Actionable Threat Intelligence Tip #1: Perform Enterprise Threat Modeling
- Geographical location
- Industry
- Organization size
- Tech stack
- And more
- Unusual network traffic patterns
- Unexpected file changes
- Anomalies in user behavior
Actionable Threat Intelligence Tip #2: Go Beyond IOCs and Gather TTPs
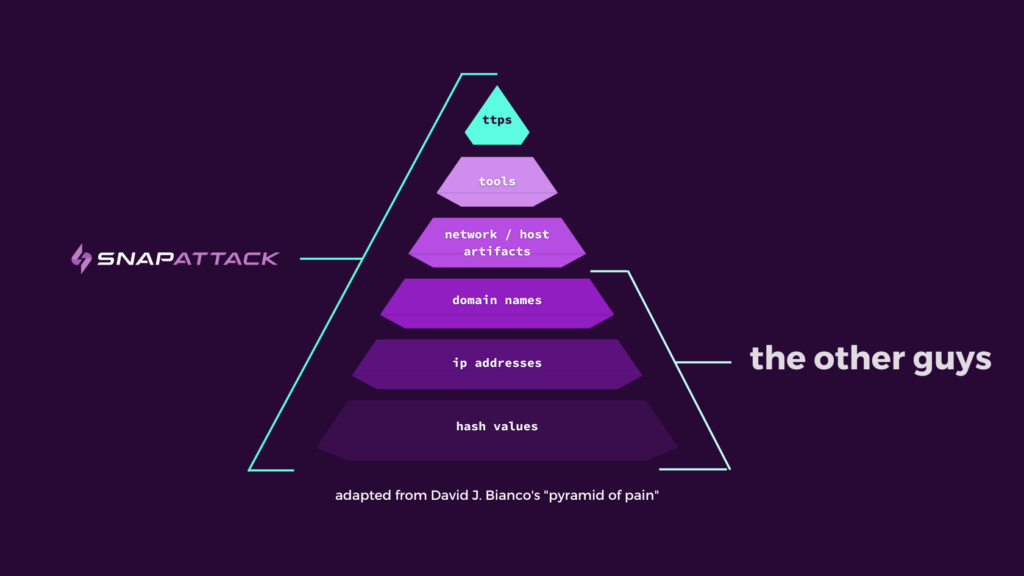
David Bianco’s Pyramid of Pain provides a stellar visual hierarchy of the differences between IOCs and TTPs. IOCs sit at the bottom of the pyramid because they’re less indicative of a specific threat actor and consist of indicators that are easy to change on the spot. Because threat hunters are actively searching for advanced, unknown threats, they need more sophisticated indicators like TTPs.
Actionable Threat Intelligence Tip #3: Provide Timely, Dynamic Insights
Actionable Threat Intelligence Tip #4: Facilitate Collaboration
Threat hunters need the ability to provide feedback on the relevance and usefulness of threat intelligence reports, as well as request additional information. Additionally, if threat hunters can simply request information, intelligence analysts don’t have to guess what tohey should investigate.
Get Threat Intelligence and Threat Hunting Teams on the Same Page
The platform ties your unique threat landscape into built-in threat intelligence from both our expert threat research team and Mandiant (now part of Google Cloud) to produce a dynamic, tailored Threat Profile. Get in touch with our team to find out how we can help you fortify your threat management today.
About SnapAttack: SnapAttack is an innovator in proactive, threat-informed security solutions. The SnapAttack platform helps organizations answer their most pressing question: “Are we protected against the threats that matter?”
By rolling threat intelligence, adversary emulation, detection engineering, threat hunting, and purple teaming into a single, easy-to-use product with a no-code interface, SnapAttack enables companies to get more from their tools and more from their teams so they can finally stay ahead of the threat.




